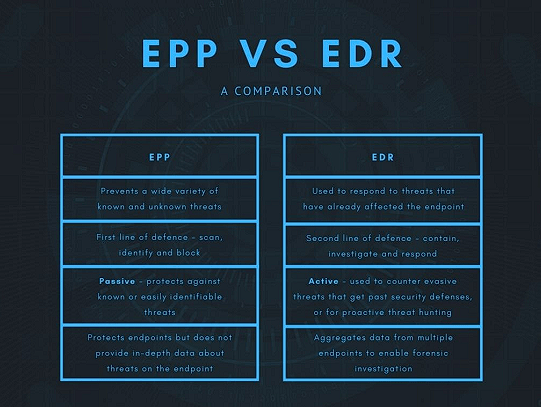
Difference Between EPP And EDR Endpoint Protection (EPP) tools help prevent malware and other threats from infiltrating an endpoint by employing signature matching, sandboxing, and other techniques to identify malicious identifiers and block access.
Modern EPP solutions gather data regarding normal endpoint behavior to detect irregular patterns and may include EDR capabilities.
Preventing Threats
EPP solutions serve as a preventative first line of defense against advanced corporate network threats, identifying file-based malware and memory-resident malicious scripts to block attacks before they take hold.
An EPP solution can detect and block dangerous URLs, prevent users from visiting spoofing pages, and protect devices against malicious scripts that exploit memory vulnerabilities. Furthermore, reasonable EPP solutions monitor endpoints offline; this feature is important since criminals often attempt to gain entry by remotely attacking businesses to upload malware or steal information to hold it for ransom.
Ideal EPP solutions should be built upon a framework that enables it to easily connect with other security products and share threat intelligence, making it more straightforward for security teams to remediate attacks using data presented on dashboards.
Some EPP solutions also feature add-on modules to increase visibility and centralize management, such as behavioral analysis that uses machine learning to identify suspicious activities and stop cyberattacks before they cause significant damage. An effective EPP can also be supplemented with endpoint detection and response (EDR) capabilities to identify advanced threats evading traditional security tools – this combination, known as extended detection and response (XDR), offers better protection by reducing alerts that overwhelm security teams.
Detecting Threats
An EPP solution can effectively ward off most malware attacks using built-in protection mechanisms, such as threat signatures. When combined with an EDR system, these frontline defenses may even detect threats that have already breached them and made their way onto networks.
A comprehensive EPP platform can integrate with security solutions that cover different areas of a cybersecurity strategy, such as mobile device management (MDM) systems or cloud monitoring services, providing protection against attacks from within and without. This ensures protection from both intruders as well as attackers.
The best EPP platforms combine multiple tools into a single interface that enables quick investigation of suspicious activity, helping reduce alert fatigue – often an issue for security teams who tend to overlook or mishandle warnings – as well as giving complete context visibility into any breaches so they can identify and respond more efficiently.
An effective EPP solution goes beyond simply integrating multiple security tools; it also leverages machine learning to increase its detection and blocking capability of threats. This capability is crucial since hackers frequently modify malware to evade antivirus detection; having an EPP platform with machine learning provides your security solution with the data it needs to identify and respond appropriately when dealing with potential attacks from cyber criminals.
Remediating Threats
An endpoint protection platform protects your organization’s data against cyber attacks that could compromise or destroy it, with advanced technologies to stop malware from infiltrating it – such as next-generation antivirus (NGAV), personal firewalls, USB device control, antimalware detection technology, deception technology, and network analytics.
Traditional antivirus and firewall tools do not detect unknown threats effectively; behavioral detection capabilities powered by artificial intelligence make this possible, enabling rapid recognition of new threats rather than waiting for signature detection – the standard practice in many antivirus solutions.
The platform is built to work on virtually all operating systems and mobile endpoints – making it simple for small or midsize businesses to gain enhanced security from the cloud without needing to install additional software on devices. Furthermore, this provides IT teams with one convenient dashboard to monitor alerts and threat information and respond faster.
An EPP solution must include the capability of monitoring and reporting on all endpoints within an organization – both online and offline – even during Wi-Fi attacks, as some threats often take advantage of this vulnerability. It should also integrate seamlessly with other security solutions like mobile device management (MDM) systems, which specialize in protecting mobile devices – this makes responding more quickly to threats or breaches affecting multiple users simultaneously easier.
Managing Threats
EPP provides security analysts with a tool for autonomously protecting primary endpoint threats, freeing them to focus on hunting down advanced attacks with endpoint detection and response (EDR) technology. Since EDR can produce many alerts simultaneously, an integrated management console for centralized control may be necessary to control it effectively.
EDR platforms that excel include real-time analytics and forensic tools to detect, investigate, and respond to threat events quickly and accurately. They feature various detection techniques – signatures, static IOCs, and machine learning-based behavioral analysis, among them – in their detection methods to help respond quickly to emerging threats. They can operate locally or cloud-based – even working without internet connectivity if necessary.
Effective EDR solutions use large amounts of telemetry to comb through massive volumes of log data for signs of attack, searching using various analytic methods and drawing upon context-rich intelligence. This allows them to identify malware not recognized by traditional antivirus software and stop attackers from seizing control of systems.
Threat intelligence allows organizations to keep hackers at bay from exploiting known vulnerabilities or hiding behind complex exploits, using deception technology like honeypots that attract attackers into an intelligence gathering trap or using third-party services like third-party threat intelligence services to detect lateral movements, suspicious connections, and remediate threat activity quickly and efficiently. Threat intelligence services also protect endpoints offline, which traditional antivirus solutions cannot do effectively.
