Cyber threats have the potential to severely disrupt an organization’s IT and network infrastructure, resulting in costly downtime, financial loss, and reputational harm.
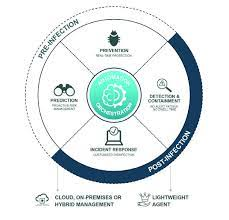
Cybersecurity teams can prevent these threats and incidents using Threat Detection and Response (TDR). TDR allows them to detect known, unknown (like a zero-day attack) and emerging risks, investigate potential compromises, and strengthen their cybersecurity measures.
What is threat detection and response?
Threat detection and response is quickly identifying threats within a network or other applications. With this capability, IT security teams can respond effectively to security incidents and mitigate damage.
Cybercriminals are relentless in their search for data and access, looking for any weak points to exploit. Often they purchase time by employing evasive malware, which bypasses antivirus, EDR (endpoint detection and response), or XDR (extended detection and response) solutions.
IT security teams and SOC analysts require better visibility into threats and integrated threat intelligence. Furthermore, they need a structured approach to reduce attacker dwell time – the longer an attacker remains undetected inside your network, the more significant damage they can do.
Managed Threat Detection and Response service
experienced team who monitors endpoints, networks, and cloud environments. These professionals are trained to detect threats quickly and take appropriate action.
Managed Detection and Response services are becoming more prevalent as organizations confront increased cyber threats. They offer organizations the ability to enhance their security posture and minimize risk without significant upfront investment.
MDR vendors employ human expertise with threat intelligence and various network, log, and endpoint detection technologies to assist businesses in detecting, containing, and responding to threats. Furthermore, they provide 24/7 monitoring services that guarantee suspicious activity is detected quickly and stopped before it causes an issue.
How Threat Detection and Response Works?
A robust threat detection and response strategy can shield your organization from data breaches, cyberattacks, and other security incidents. It also assists in adhering to industry regulations while identifying vulnerabilities before malicious actors exploit them.
Detecting threats requires a combination of humans and technology. Security analysts examine trends, patterns in data, and behaviors to determine whether anomalies indicate an actual threat or false alarms.
The technical component involves security tools that scan a network for suspicious behavior and data in real time, alerting the security team when an attack is discovered. These instruments prioritize risks to enable quick responses, helping minimize damage and speed up recovery time.
Effective cybersecurity solutions must be designed to detect known and unknown threats. Cybercriminals often circumvent traditional security measures by employing native operating system tools or open-source attack software on target systems without detection.
Methods and Types of Threat Detection and Response
Threat detection encompasses a range of methods and types, each designed to help identify known threats or patterns of malicious activity. Some examples include data mining, pattern recognition, and anomaly detection.
Behavioral modeling can also be employed to detect cyberattacks. It involves examining an attacker’s behaviors and tactics.
Indicators of compromise are digital pieces of evidence that can assist administrators in determining if an attack has occurred or is currently occurring. These may include indications of unauthorized access, unusual activity, and changes to system configurations.
Indicators of compromise are an integral component of security operations. It helps cybersecurity teams in directions of known, unknown (like zero-day threats), and emerging risks early on.
Threat Detection and Response Systems Tools and Software
Threat detection systems are an integral component of any cybersecurity solution. They include intrusion detection systems, anti-malware programs, and other tools that help detect malicious activity on your network.
Intrusion detection systems monitor log files and send alerts if suspicious activity is identified. They also employ automated detection strategies to save time by eliminating manual intervention.
Another type of security measure is a host intrusion detection system (HIDS). These programs collect, store and search log files to detect any signs of malicious activity or intrusion.
HIDS usually offers customizable rules and policies, enabling you to specify what actions the software should take when it detects an intrusion. They also provide other features like anomaly-based detection and IP geolocation.
