EDR is also known as Endpoint detection and response which is a cybersecurity technology that monitors and detects endpoint threats. This enables security teams to detect malicious attacks quickly, avoiding further collateral damage.
EDR tools collect information on processes, communications and user logins occurring on an endpoint device. This telemetry gives the security team a complete view into endpoint activity.
WHAT IS ENDPOINT DETECTION AND RESPONSE?
Many consider EDR to be a top-of-the-line security solution, and for good reason. Housed in an impressive locked box, it acts as an all-inclusive hub for desktops, servers, mobile devices and more – all while taking up minimal space in standard rackmount or on-premise data centers. Staying secure in today’s ever-evolving digital world can be no small feat – which makes the EDR one of the smartest moves you can make in this digital age.
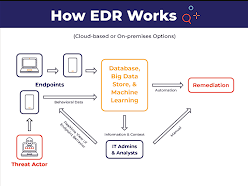
How Does EDR Work?
EDR technology employs advanced algorithms to detect behavior that is out of the ordinary for a particular user. This data is then filtered, enhanced, and monitored for signs of malicious activity.
Once a threat is identified, security teams and stakeholders are informed. Analysts can then investigate the threat and take necessary actions to mitigate it.
An effective EDR solution can act quickly to contain malware and other threats before they have a chance to spread or cause harm to the rest of the system. Furthermore, it stores data for analysts and threat hunting teams so they can conduct further investigations with confidence.
An effective EDR solution can also prevent and protect against ransomware, spyware, and other sophisticated threats. This capability offers businesses peace of mind in the event that an unknown threat infiltrates their network.
What is an edr and its Functions
Endpoint detection and response (EDR) monitors your network to detect suspicious activity and sends alerts to security teams. It also automatically initiates responses in response to certain triggers.
EDR is a crucial element of any cybersecurity plan, as cybercriminals are increasingly targeting endpoint devices as easier targets.
Detection of these threats can provide your team with invaluable information about their origin, which parts of your network were affected, and how to prevent them from spreading further.
Analysts will need to sift through alerts, but an EDR solution can help ease this burden with optimized automated responses. This reduces alert fatigue and gives analysts more time for other tasks.
What is an EDR and its Important?
EDR is an integral element of an effective endpoint security strategy. Without it, attackers could linger inside your network for weeks or months without detection.
EDR utilizes continuous monitoring and data collection to detect threats as they emerge, giving security teams time to respond and mitigate damage quickly. Furthermore, this type of security solution reduces alert fatigue for security analysts while keeping them more engaged and productive on the job.
To be effective, an EDR tool should provide a comprehensive range of capabilities like continuous file analysis, forensic investigation and behavioral analysis. Furthermore, ideal solutions should offer broad visibility as well as machine learning-based attack detection. Independent tests like MITRE ATT&CK Evaluation can help organizations determine which tools are most suitable for their requirements.
What is an EDR and its Capabilities
Endpoint detection and response (EDR) security solutions offer specialized tools to assess and respond to security incidents. These capabilities may include detection, prevention, forensics and threat intelligence.
Automated response features can free security teams to focus on more strategic work, like threat hunting. They also help in activities such as preventing compromised processes, alerting users and disabling suspect endpoints and accounts.
Detection: EDR technology employs behavioral analysis and big data to detect suspicious activity that may go undetected by firewalls, antivirus and other frontline defenses. For instance, an effective EDR solution can automatically detect stealthy attackers by analyzing file behavior in real time.
Some EDR solutions utilize threat intelligence to provide context for attacks by comparing network and endpoint activity with real-world examples of known cyberattacks. With this data, EDR can identify and respond to threats more rapidly and precisely.
See Also:
