EDR tools are an essential part of your cybersecurity arsenal, providing the ability to detect, investigate and respond quickly to cyber attacks that bypass prevention measures.
EDR solutions monitor threat data on endpoints and aggregate it to provide a consolidated view of threats while providing forensics and incident response capabilities.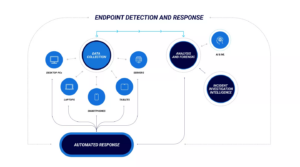
Real-time monitoring
Real-time monitoring is fundamental to an endpoint detection response (EDR) solution. EDR solutions work proactively against malware and other threats using machine learning technology to identify anomalous behavior. If they detect something malicious, EDR solutions take appropriate action: alerting stakeholders of security incidents, blocking access or cutting off communication altogether.
EDRs can also help shorten mean time-to-respond (MTTR), an essential metric in cybersecurity. EDRs allow security teams to detect and respond more rapidly to attacks than with traditional antivirus software alone, helping security teams anticipate and remedy weaknesses before attackers exploit them.
Data analytics can also help businesses and customers improve business processes and customer experiences. For instance, tracking real-time data can assist call centre agents in performing better by tracking agent performance in real-time and analyzing real-time information to identify areas where agents are struggling and make necessary improvements; additionally, it may allow you to determine if specific customers may abandon their calls before it happens.
Real-time monitoring provides businesses with another cost-cutting strategy to safeguard productivity and avoid costly system outages that can negatively impact productivity and lead to financial losses – for instance, when an online retail website loses service due to server failure, it could result in lost revenues and customers. Real-time monitoring also has environmental science applications, including measuring river flow, air and water temperatures, ocean chemistry, wind speed and direction.
Incident response
Maintaining an incident response plan is essential to mitigating cyberattacks or other incidents that disrupt business operations. A detailed incident response plan should include details regarding roles, responsibilities, communications plan and processes, as well as tools/technologies needed for handling an incident.
Not only should you have a comprehensive plan in place, but employees should also be educated on its significance. Helping staff understand its purpose may reduce their likelihood of falling prey to ransomware or other threats.
An EDR solution should enable you to locate and investigate all forms of threat activity, from APTs to real-time traffic anomalies and reconnaissance attacks. Furthermore, EDR should integrate with threat intelligence services for greater context around attackers’ motivations.
Idealistically, organizations should employ a team of specialists that can respond swiftly and effectively to all types of incidents. A diverse team can help respond more rapidly and detect new vulnerabilities more readily; having a formal incident response plan may speed forensic analysis while lowering breach risks and save more complex business continuity and disaster recovery plans from needlessly invoking.
Threat intelligence
Threat intelligence is an integral component of EDR, helping security teams understand an attacker’s tactics, techniques and procedures (TTPs) to anticipate his next moves proactively and shift cybersecurity from reactive to proactive mode.
Threat Intelligence is the ongoing practice of collecting, processing, analyzing, disseminating and sharing cyberattack data gathered through human interviews, antivirus logs or network sensors.
Third-party threat intelligence services can enhance the effectiveness of EDR solutions by providing access to a global repository of threat data and characteristics, which enables organizations to detect exploits that would otherwise remain undetected through traditional means. Such capabilities are especially crucial when recognizing sophisticated malware or multilayered attacks.
Tactical threat intelligence can be generated quickly and automatically yet has a short shelf life – indicators of compromise (IOCs), such as bad IP addresses or malicious domain names, can become obsolete within days. More sophisticated systems can map IOCs to the MITRE ATT&CK framework to better inform IT teams of observed behaviour.
Strategic threat intelligence provides longer-term insights, informing non-technical stakeholders, CISOs and CIOs of potential risks to make wise investments and mitigate risk better; additionally, it assists them with making cybersecurity strategies which align with business goals.
Automation
Automating endpoint detection response strategies (EDR) can help your organization detect and respond to cyber threats quickly and efficiently. EDR solutions can send alerts directly to staff when they identify threats and take actions based on pre-configured rules; additionally, these tools can analyze data to detect anomalies or suspicious activity while offering insight into your security threat landscape.
EDR stands out by continuously monitoring all endpoints, including remote workers, so you can detect threats instantly and halt their spread. Furthermore, it provides visibility into the threat landscape from one central console and can detect and respond to threats within seconds to reduce cyberattack impacts on your business.
EDR also can assist in identifying and correcting vulnerabilities within your network before they become full-scale breaches. Best practices for endpoint security should include installing strong antivirus and anti-malware solutions, keeping software updated, and enforcing stringent password policies.
Xcitium’s EDR platform utilizes correlated telemetry to map endpoint processes and activities against their environments for visibility into the threat landscape. Its architecture includes a situational model that facilitates rapid investigations and remediations by quickly providing details and context at scale.
