Endpoint Security protects against cyberattacks on all the devices connected to your network – such as laptops, computers, tablets, smartphones, and IoT devices. These include laptops, computers, tablets, smartphones, and IoT devices.
Most cybersecurity systems rely on signatures and threat intelligence to detect threats; however, these methods may produce many false alarms, leaving your team to spend hours investigating false alerts.
What is an Endpoint Security Solution?
Endpoint security solutions proactively protect devices connected to a business network from cyberattacks, such as smartphones, laptops, tablets, and desktops used by employees in the office or remotely for work purposes. With cybercriminals developing sophisticated methods for bypassing firewalls and breaching enterprise perimeters, businesses need advanced cloud-powered endpoint protection tools for maximum protection of endpoint devices.
These tools often include antivirus software but go far beyond simple antimalware detection to provide comprehensive device protection against all threats that can compromise devices.
Sandboxing technology isolates files and programs to be tested against their intended environments for improved malware detection and reduced false positives; device management prevents unapproved apps from running or removes them when no longer necessary; they may even offer encryption protection of sensitive data.
Finally, solutions should be scalable, enabling administrators to monitor and manage various endpoints from one central dashboard while using agentless technologies that reduce endpoint bloat. Cloud solutions provide greater performance while keeping administration costs at bay, increasing coverage, and improving overall performance.
Endpoint security solutions protect from phishing attacks using sophisticated tactics such as watering holes and exploit kits, device loss/theft, which is one of the primary causes of data breaches for small to medium-sized businesses, and ransomware attacks by detecting and blocking malicious behavior on devices, as well as ransomware attacks which seeks to gain entry through exploit kits or ransomware attacks on devices.
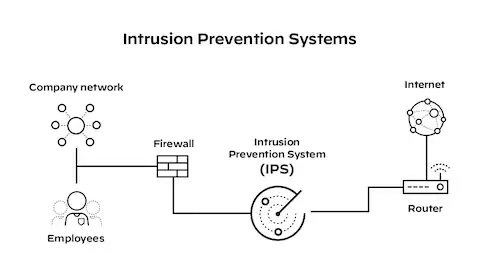
What is an Intrusion Prevention System?
An intrusion prevention system (IPS) monitors network traffic in real-time. It compares it with known patterns of threats and attacks, sending alerts when any unusual activities that don’t fit within expected patterns are identified. When generated, an alert may trigger human administrator alerts, drop packets, block traffic to and from affected IP addresses, obfuscate attacks for cybercriminals to identify, or obfuscate them entirely to make detection more difficult.
Signature-based and anomaly-based detection are two main techniques IPSs use to identify malicious activity, with signature-based detection being viral among enterprises.
Signature-based detection employs fingerprinting technology to track threat activity. It creates a database of typical attack patterns, which are then compared against network traffic to identify and block potential threats quickly and accurately – ideal for cyberattacks that elude other security technologies but are less valuable against new vulnerabilities or zero-day exploits.
An anomaly-based detection solution effectively protects against newer cyberattacks and stops them before they succeed. Such intrusion prevention systems (IPSs) detect abnormal network behaviors, which may indicate new malware that escapes other security solutions; additionally, they can detect any attempts by intruders to gain access to sensitive data or shut down a server without authorization – something an IDS might miss altogether. Anomaly-based IPSs may also be combined with one to maximize effectiveness and decrease solution fatigue.
What is the Difference Between the Two?
Antivirus software, firewalls, and device controls are found in both solutions; however, endpoint security provides additional features designed to defend devices against various threats.
Endpoint security is part of cybersecurity solutions that help defend endpoint devices like PCs, tablets, mobile phones, and IoT devices against cyber attacks.
An Intrusion Prevention System (IPS) monitors network activity to identify potential cyber threats, and its primary goal is to stop malicious traffic before it can cause any damage. IPS solutions use both signature-based detection methods (using known attack signatures to compare current traffic against) as well as anomaly-based detection (which analyzes current data against baseline standards, looking for patterns that might indicate new attacks or zero-day vulnerabilities that attackers use before software developers have time to release updates) to achieve this objective. To do this effectively, they employ both these detection methods simultaneously – signature compared against known attack signatures identifies abnormal patterns. In contrast, anomaly-based detection detects unusual traffic by comparing current traffic with databases of known attack signatures. In contrast, anomaly-based detection can even block zero-day vulnerabilities used by attackers before software developers can release updates on such vulnerabilities used by attackers before software developers have time to issue fixes or by both approaches simultaneously.
IPS solutions can be deployed as standalone systems or integrated into next-generation firewalls (NGFW). In either instance, these IPS systems must be placed “inline” within your network to function and dramatically lower enterprise security risk by intercepting threats before they can impact an organization.
Which is Better for Your Business?
As remote work cultures flourish, employees need access to their systems from anywhere. But devices must remain protected against cyberattacks – that’s where an endpoint security solution comes in handy; such solutions protect laptops, tablets, computers, and IoT devices against threats that bypass network security measures.
Some of these solutions provide antimalware, data encryption, and device and application control to provide multiple layers of protection, making it much harder for attackers to breach an organization’s system.
An Intrusion Prevention System (IPS) is a security solution that monitors network traffic in real-time and blocks malicious activity, blocking it instantly. IPSs typically feature as part of Unified Threat Management or Next Generation Firewall solutions; they may also be purchased separately as standalone offerings. They usually sit “inline” on networks to quickly identify and block suspicious traffic; this helps other security controls increase performance by decreasing the workload burden.
IPSs can be either host- or network-based and use signature-based or anomaly-detection methods to detect malicious connections. Numerous different IPS models are available; selecting one suitable for your business is essential. It should protect from multiple threats without creating additional risks or cost increases.
