How To Test EDR Solution An effective EDR solution protects at the perimeter (EPP) and within its environment (EDR), providing complete visibility of threats outside and within to detect, respond to, and contain them before they cause significant harm to networks or infrastructures.
An EDR solution captures and analyzes endpoint telemetry data – similar to “black box” information from computers – to quickly detect threats. Furthermore, EDR solutions support forensic investigation capabilities and rapid response tools for immediate mitigation measures.
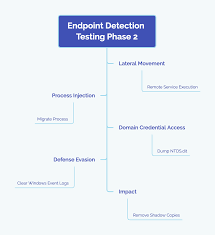
Real-World Testing
An effective EDR solution enables security teams to identify every potential threat on their network by collecting endpoint telemetry and transmitting it back to a central management console for viewing by security personnel. From here, investigations and response plans can be launched across all endpoints. EDR solutions may also integrate with Security Orchestration Automation and Response (SOAR) systems to run threat detection playbooks automatically against identified threats.
EDR solutions differ from antivirus or firewall software in focusing more on detection, analysis, and response to advanced threats that have gained entry to a network. EDR should detect even stealthy malware that quickly switches between benign and malicious files – look for EDR solutions with deep investigative capabilities that can determine how a threat entered your network in the first place.
For an EDR solution to be effective in real-world environments, ask about its vendor’s method for testing its product against different enterprise environments. An ideal test would use multiple real-world threats that resemble exploit kits and ransomware attacks instead of typical security tests, which simulate just one type of attack at a time. In addition to simultaneously simulating attacks from all possible angles, this type of evaluation should also evaluate whether security expert human reviews exist and any false negative rate impact that this solution might have on effectiveness.
Security Operations Center (SOC) Tests
EDR security solutions offer similar information after an incident, providing key insights to stop future attacks and uncover past ones. EDR uses an approach similar to flight data recorders by gathering information about each endpoint, such as processes running, programs installed, and network connections. SOC can then analyze this data to detect what could have led to an attack and be utilized against any subsequent threats that might emerge from within an enterprise.
SOC teams must closely scrutinize any alert generated by monitoring tools that detect suspicious activity to eliminate false positives and assess potential threats. They then triage alerts according to urgency – shutting down or isolating devices with infection, stopping harmful processes from running, deleting files etc. SOC staff must maintain meticulous records of alerts received, ranking each accordingly so no security threats go undetected.
An effective SOC requires an expert security team. Ideally, Members should possess knowledge in fields like computer engineering, cybersecurity, or network engineering and credentials like the CISSP or GIAC. A SOC manager reports directly to their CISO, while analysts, security engineers, and other staff provide security expertise and support. A reliable SOC must regularly conduct vulnerability assessments and penetration tests while staying abreast of new threats, solutions, and best practices.
Detection Tests
Every device that connects to your network presents potential entryways for cyber threats, from employee workstations and laptops, mobile phones, servers, IoT systems, and cloud apps – not only antivirus solutions but also legacy endpoint protection solutions have become insufficient against modern attacks such as ransomware or phishing attacks.
An EDR solution can detect these emerging threats by analyzing data to spot suspicious activity, alerting security operations teams to anything out of the ordinary that could indicate a breach, collecting and analyzing endpoint telemetry (such as system events, processes, drivers, registry changes, disk accesses memory accesses network connections, etc.) which provides invaluable data that helps speed up investigation and containment processes as well as reduce time and impact to your business.
An EDR security solution must provide visibility and context so analysts can make informed decisions regarding an adequate response, whether eliminating or quarantining threats. An EDR solution should only reveal actionable detections while hiding irrelevant data to prevent alert fatigue.
SE Labs conducts EDR solution tests by simulating real-world scenarios reminiscent of enterprise environments – simulating normal and malicious activities for testing accuracy over what other vendors typically provide.
Reporting Tests
EDR tools offer visibility into suspected attacks and enable security teams to react swiftly, monitoring endpoint data and user activity to detect anomalies and conduct deep analysis. EDR tools use real-time alerts to notify and prioritize cyber threats for investigation and response; some automatically trigger specific responses, such as quarantining infected files or deleting them, while others take preventative actions like mandating password complexity requirements or two-factor authentication for accessing networks.
EDR solutions offer visibility into the complete state of an organization’s endpoints from one central management console and threat response capability through integrations with other security tools and a SOAR platform (security orchestration, automation, and response). Some EDR solutions incorporate baselining, behavioral analytics, and contextual analysis to identify elusive threats that might otherwise go undetected; other EDR products utilize fileless detection or evasion methods to counter malware attacks.
Conduct technical and performance testing of EDR solutions to assess their capabilities and compatibility with your environment. Testing should include proof-of-concept evaluations, pilot deployment trials, or actual implementation assessments to gauge their impact on existing infrastructure and workflows. You should also utilize industry reports from reliable sources for comparative analyses of EDR products.
