Your computers and IoT devices that power your business require endpoint protection to detect threats, flag suspicious activities and prevent infections with malware. This provides important safeguards to help prevent threats, track suspicious activities and stop potential infections.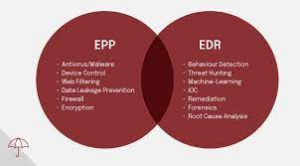
An effective EDR solution should utilize cloud-based detection technologies to access real-time threat data, eliminating security silos and optimizing protection performance, as well as automating incident response processes.
Detection
Endpoint security platforms use antivirus to guard against traditional threats like malware but also require EDR capabilities to detect and investigate advanced attacks that bypass basic measures – like zero-day attacks, ransomware, file-less attack methods and other techniques that bypass traditional detection mechanisms.
EDR solutions with integrated forensic analysis capabilities can assist you in rapidly gathering context on threats to assess their nature, how they entered your network, their location and impact or damage on systems – which can help take more timely and appropriate measures against them. This can assist with mitigating them before spreading further or taking preventive steps against emerging threats.
EDR solutions differ from traditional antivirus and firewall products in that they proactively search for unknown threats through behavioural approaches. Telemetry data collected, analyzed, and contextually enhanced is examined to detect anomalies that could indicate an unknown or unknown threat.
EDR solutions provide automatic responses to threats by shutting down processes, quarantining files or isolating endpoints as necessary to stop them from spreading further. This saves both your team time and effort in responding to breaches by freeing them up for more pressing business needs – while saving money by discouraging hackers from doing further damage in future attacks.
Prevention
Endpoint protection platforms reduce your attack surface by blocking malicious files from infiltrating your system, ingesting data on endpoint behaviour to detect anomalies and identify threats, and taking automated or manual actions like deleting files, isolating endpoints from networks, wiping reimaging devices to eliminate infections from devices.
Traditional antivirus software (commonly referred to as legacy AV) utilizes recorded indicators of compromise and behavioural patterns to filter endpoint data. Still, malware authors can alter their code faster than security professionals can modify AV software accordingly – meaning traditional AV may detect trojan or ransomware infections but will likely miss more advanced attacks.
Next-generation endpoint protection solutions like SentinelOne provide an answer by assessing each running program instead of just relying on preconfigured threat parameters. SentinelOne detects whether programs exhibit signs of malware such as taking over system processes or stealing data and encrypting it – and alerting both user and security staff if their behaviour changes. At the same time, machine learning helps strengthen detection over time.
Response
Endpoint protection platforms (EPPs), designed to reduce an organization’s attack surface by blocking malware and other threats, reduce its surface by blocking malware and threats posed by mobile devices, laptops, desktop computers and servers in its network. EPPs work effectively against exploited vulnerabilities across these devices that comprise an organization’s network – including mobile phones, laptops, desktop computers and servers – thereby protecting it against further breaches in security.
Modern EPP solutions go beyond legacy antivirus software’s signature-based detection by using behavioural-pattern analysis and process inspection techniques to detect and block known malware based on its characteristics and behaviour patterns. They can even identify fileless threats such as fileless ransomware using various techniques like monitoring behavioural patterns and inspecting running processes.
EPPs use cloud-based databases of threat information instead of maintaining one locally, which eliminates the bloat associated with maintaining databases regularly and speeds up response time and remediation efforts. Many solutions also feature automated incident response and remediation capabilities for security teams to save manual work hours.
EPP solutions alone do not always protect from attacks that bypass frontline defences, so an EDR solution must be utilized as a part of your organization’s prevention tools to detect threats after they gain control of endpoints and infiltrate networks. After identification, automated or manual actions such as isolating affected devices from networks, wiping and reimaging them or stopping malicious processes may occur automatically or manually depending on what actions were initiated by an attacker. Ideally suited EDR solutions offer contextualized threat-hunting capabilities to detect signs that other prevention mechanisms might miss.
Integration
If you are using multiple endpoint protection tools to secure digital assets, they must work cohesively together. Furthermore, it would help if you had a central management console to monitor these tools to reduce the IT team’s burden and eliminate the risk of missing updates or responding to false positives.
At its core, an EPP solution should protect from cyberattacks in several ways: next-generation anti-malware (NGAV) that detects attacks from malware, exploits, LOLBins and Macros; heuristic threat algorithms and behavioural monitoring to detect hidden fileless and advanced threats; patch management so all systems remain up to date; keylogging prevention; deception technology to attract attackers into honeypots for data collection purposes; etc.
As part of your solution selection, ensure it can automatically deploy security updates and patches across your devices. This reduces IT staff workload, freeing them up for more productive projects. Seek a cloud-based EPP that’s quick to install, easy to scale and offers a centralized management console – finding one with all-in-one services such as XDR, Response Automation, and 24/7 MDR would be even better!
