Advanced threats will eventually breach your security barriers, so when they do, you must respond and detect them quickly before they steal data or cost your business money.
EDR can help with that – this security solution combines continuous real-time monitoring, collection of endpoint data and automated response capabilities to eradicate threats quickly.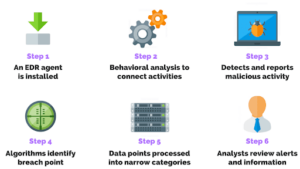
Endpoint Detection and Response
EDR stands apart from antivirus and firewall solutions because it uses behaviour analysis capabilities to identify suspicious commands or processes on endpoints. When threats are identified, an alert is generated, and action will be taken automatically on that specific endpoint – including quarantining files that contain harmful code, removing it from the system altogether and taking other automated or manual measures necessary to stop their threat.
As cyberattacks continue to evolve and grow more sophisticated, it is becoming more critical that organizations of every size implement effective cybersecurity tools that can protect them against these attacks. With ransomware and malware threats such as ransomware threatening operations and exposing sensitive information, security teams need swift and reliable ways of detecting any breaches quickly and reliably – such as an EDR security tool equipped with rapid response features that will eliminate damage as soon as it occurs and protect from costly data breaches.
EDR security solutions monitor endpoints (workstations, servers and cloud workloads) and their network connections, recording all activities. These records, also known as event logs, allow for increased detection of attacks that might otherwise go undetected. EDR tools integrate seamlessly with existing cybersecurity tools and systems to analyze suspicious activity before responding accordingly.
EDR solutions not only monitor and detect threats; they also serve as incident response and forensics solutions. For instance, EDR solutions can capture images of infected endpoints and then use these images to reimage or roll back them, eliminating the threat. Furthermore, EDR can help investigate an attack, including its origins, how it entered networks, which files were affected, replication efforts, and its replication potential.
EDR tools typically collect and aggregate endpoint data, enabling analysts to derive insights manually. While more basic EDR tools focus on collecting aggregated endpoint data for analysis by analysts, more advanced EDR tools provide automatic pattern and anomaly identification using AI algorithms and machine learning to streamline the logging process and provide real-time alerts. Furthermore, more sophisticated EDR tools may also correlate security events from endpoint, network and SIEM security tools to reveal new attack vectors or resolve ongoing incidents that might have otherwise gone undetected, providing your security team with access to intelligence in real-time so they can swiftly act against any threats infiltrating the network.
Endpoint Protection Platform
An EPP provides powerful response capability against alerts and cyberattacks in networks, email systems, cloud environments and more.
An EPP is often coupled with an Extended Detection and Response (EDR) solution to create an extended detection and response system (EDR). An EDR adds further visibility by tracking every file execution, registry change, network connection or binary run on all endpoints and workloads – providing security teams with continuous insight into what is happening at their endpoints and any suspicious activities occurring behind the scenes.
EPPs require real-time threat data to be effective, which allows them to monitor attackers and their methods as they evolve. Furthermore, advanced EPP solutions offer advanced detection capabilities utilizing various mechanisms, including signatures, behaviour analytics and machine learning – which allow these technologies to identify threats that traditional antimalware software cannot or has missed completely or new threats discovered through device behaviour analysis.
When selecting an EPP, look for one with a local agent capable of operating independently from corporate networks and without being dependent upon an internet connection to access its management console. Furthermore, look for solutions with global databases of ongoing threat activity that can ingest information from outside your network to increase attacker behaviours’ detection abilities.
Many EPP vendors provide managed detection and response services via their own SOC or an affiliated partner’s SOC, providing certified SOC experts and up-to-the-minute threat intelligence at an affordable monthly fee. This can reduce security teams’ operational and monitoring burden while freeing them up for more crucial activities such as threat hunting, incident response or other key duties.
An EPP can simplify security stacks by consolidating multiple solutions into a centralized solution. An enterprise may employ various antivirus and firewall protection tools to safeguard its network and remote employees. An EPP equipped with an integrated, centralized management and monitoring system streamlines security operations and enhances performance, helping organizations ensure the appropriate security controls and quickly adapt to changes in the threat landscape. As malware becomes more advanced, security teams must utilize a system capable of adapting quickly to block attackers from breaching the network. EPP with EDR capabilities enables teams to detect and respond to cyberattacks quickly.
